|
|
 |
i-Security Vulnerability Management System (VMS™)
Yesterday meant fragmented security solutions with disparate
threat data and a complete lack of centralized policy enforcement
and compliance reporting.
Today we offer a better way to reduce your risk - consolidated endpoint security management with the
i-Security Vulnerability Management System™
|
|
|
|
 |
|
Actionable Reporting |
| |
Top 20
"Top 20" options such as Vulnerabilities by OS,
Top 20 CVE and Top 20 SANS
Composite Assessment Compliance
Combination of the network-based assessment
and agent-based assessment compliance
reports
Executive Summaries
High-level view of vulnerabilities found for a
selected scan job and by OS
Vulnerability Detail
Customized level of detail about each asset
Network Inventory
Inventory information such as OS, MAC, IP,
NetBIOS
Vulnerability Set Configuration
Cross reference of all the vulnerabilities in the
VMS™ database
Scant Configuration
Discovery and management options used by a specific job
Scan Summary
Summarized list of vulnerability counts by
target
Ports and Banners
Ports discovered "listening" or open
Local Services
Number of unique services found by the scan,
including services found on each target
Short & Long Term Trending
Comparison of results between two scans,
and data changes over time for multiple scans |
|
 |
|
Vulnerability Management System |
| |
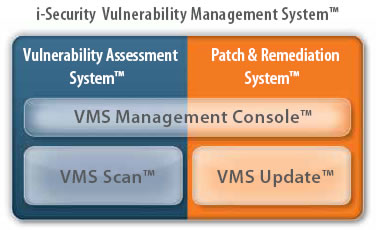
The i-Security Vulnerability Management System enables you to effectively manage the entire vulnerability lifecycle - assessment , remediation, audit and reporting – all from within a single, proven
solution.
The i-Security Vulnerability
Management System
combines the network -
based vulnerability scanning
of VMS Scan™ with the
agent-based assessment and
patented remediation of
VMS Update™ into a unified solution under a central management and reporting console that delivers:
- Thorough discovery and inventory of all network assets
- Automatic propagation of agents to rogue computers
- Accurate network- and agent-based threat assessments
- Patented vulnerability remediation
- Validation of compliance with security policies
- Comprehensive Reporting
- Consolidation of security resources
|
|
 |
|
A Proven Process |
| |
i-Security delivers complete vulnerability management through a market validated process that includes complete asset
discovery and inventory, comprehensive assessments based upon network-based and host-based scans, intelligent,automated remediation and ongoinh policy complicance audits - all from a single,management console for a unified view and enterprise wide reporting.
Comprehensive Threat Assessment
with VMS Scan™
Intelligent Remediation and Validation
with VMS Update™
Centralized Management & Reporting
with VMS Security Management Console™
(Enterprise or Standard Version)
VMS Scan™ :
Network-Based Vulnerability Assessment ( 2 )
VMS Scan™ provides accurate and thorough
network-based (agent less) vulnerability assessments using safe,flexible scanning techniques.Once threatsremediation based upon vulnerability scoring and
are identified, VMS Scan™ helps you prioritize them for
asset criticality.
- Flexible network-based scanning techniques based
on access-levels, including credentialed and null based
scans.
- Broad scans of every device on your network,
including servers, printers, routers, wireless access
points, and many more.
- Detailed assessment checks on security configurations, antivirus, sharing tools, worms, Trojans, missing
patches, open ports, services and more.
- Designed to safely scan for vulnerabilities with
minimum impact to your network by never employing
malicious attacks. Scanning methodology uses safe,
standard networking protocols.
VMS Update™ :
Agent-Based Assessment & Remediation ( 3 )
VMS Update™ provides automated patch deployment
and ongoing audits of applied patches for proactive
security and continuous policy compliance.
VMS Update™, the market-leading patch management
solution, enables you to patch more machines, faster
and more accurately than ever.
- Scalable, agent-based architecture that reduces
bandwidth consumption and ensures security of
mobile computers that are often removed from the
network
- Flexible, role-based administration with Active
Directory integration enables the delegation of
agent/group anagement, assessment and remediation
activities to improve productivity while maintaining
security
- Mandatory Baseline capability that provides
automatic support for security policy enforcement.
- World’s largest patch repository of pre-tested
patches and security updates that delivers completecoverage for heterogeneous nvironments.
VMS Security Management Console™:
Central Command and Reporting ( 2 - 5 )
The VMS Security Management Console provides
centralized, role-based management of VMS
assessment and remediation engines, a consolidated
view of all threat management activities and a central
source for report generation.
- Performs a thorough discovery and prepares an
accurate inventory of all network assets - routers, printers,
servers, laptops operating systems, switches,
wireless access points and more. ( 2 )
- Automatically propagates agents to unmanaged
(rogue) computers for complete protection. ( 3 )
- Enables enterprise-wide command and control of
agent less or agent-based scans, policy enforcement,
patch distribution, inventory mgmt, and more. ( 4 )
- Aggregates the vulnerability assessment and remediation
results from various VMS Scan™ and VMS Update™ engines across a true n-tier network, into a single point
for local or enterprise reporting. ( 5 )

|
|
|
 |
|
i-Security VMS™ Specification:
|
| |
| |
VMS-150 |
VMS-500 |
VMS-500e |
VMS-1000 |
VMS-1800 |
| |
 |
 |
 |
 |
 |
| Scanner |
Included |
Excluded |
| Patch Distribution |
Included |
| Management Console |
Included |
| Client OS Support |
All Windows OS, Linux,MAC OS,Novell,Solars,HP UX,AIX,Blackberry. |
| Form Factor |
1U |
2U |
2U |
2U |
2U |
| Management |
Console
/Remote/Web |
Console
/Remote/Web |
Console
/Remote/Web |
Console
/Remote/Web |
Console
/Remote/Web |
| Base Network Interface |
4×10
/100Mbps |
2×10/
100/1000Mbps |
2×10/
100/1000Mbps |
2×10/
100/1000Mbps |
2×10/
100/1000Mbps |
| Maximum Network Interface |
Null |
4GE,copper/fiber |
6GE,copper/fiber |
6GE,copper/fiber |
6GE,copper/fiber |
| Fiber Interface |
No |
Yes |
Yes |
Yes |
Yes |
| Memory |
1GB/1GB |
1GB/2GB |
1GB/4GB |
2GB/4GB |
2GB/8GB |
| Storage |
36GB |
36GB |
72GB |
72GB |
72GB |
| Base Clients |
50 |
100 |
250 |
500 |
0 |
| Maximum Clients |
150 |
500 |
2000 |
5000 |
10000 |
| Redundant HDD |
No |
Optional |
Optional |
Optional |
Optional |
| Redundant Power Supply |
No |
Optional |
Optional |
Base |
Base |
|
|
|
|
|
|
|